Scam Alerts
8 Scams That Senior Medicare Patrols Are Seeing Now
Old deceptions are recycled to take advantage of what you know from news reports
Identity Fraud Cost Americans $43 Billion in 2023
Victims are losing more money to these crimes, a new AARP-backed report finds
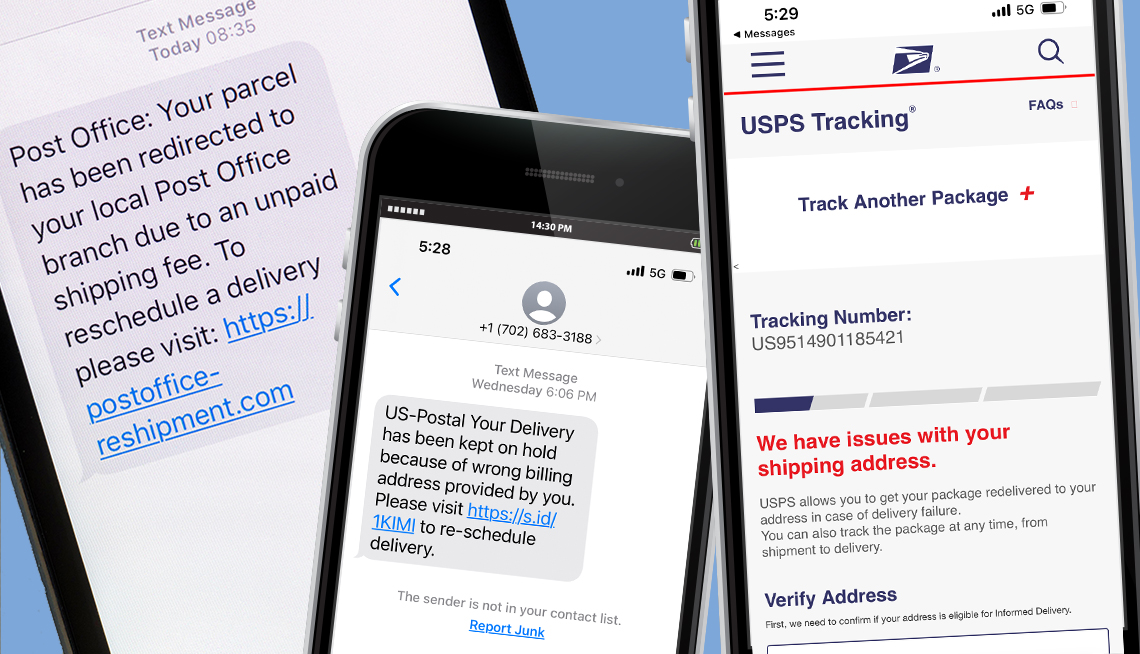
Fake Delivery Service Text Alerts Are Rampant
How to tell if messages are legitimate or criminals’ smishing attempts this holiday season
Is That Your Bank Contacting You — or a Scammer?
Criminals pretend to warn you about fraud while trying to steal your money
Beware of ‘Do Me a Favor’ Scam Messages
An increasingly common scheme involves impostors claiming to need help buying gift cards
How to Avoid Scams on Zelle, Venmo and Other P2P Apps
Criminals love peer-to-peer payment methods; learn to use them safely
6 Top Scams to Watch Out for in 2024
Criminals are getting more sophisticated and supercharging old scams with new technology
Scammers and Celebrity Impostors Defraud Fans
Singers Blake Shelton and Dolly Parton are among the many stars impersonated
Fraud Fighting
What to Do if Your Wallet Is Lost or Stolen
7 steps to prevent identity theft and money loss — plus how to replace what’s missing
How to Avoid Scams on Facebook Marketplace
Scammers aim to take advantage of both buyers and sellers. Here’s how to spot and avoid them
Avoid Real Estate Wire Fraud When Buying a Home
A New Jersey couple lost nearly $92,000 to scammers — and they’re not alone
How, Why and When to Check (or Freeze) Your Credit Score
Monitoring your creditworthiness is key for tracking your financial health and spotting fraud
10 Worst Things to Carry in Your Wallet
With identity theft rampant, keep only the essentials in your pocket or purse
White House Announces New AI Protection Efforts
Measures meant to prevent fraud, keep infrastructure secure and protect privacy
Victim Support
AARP's Fraud Watch Network Helpline Is Fighting for You
Volunteers provide emotional support and practical advice to scam victims
3 Ways to Help a Loved One Who Has Been Victimized
Ease the burden on your friend or family member by offering compassion, assistance
Elder Fraud
The Legal Consequences of Elder Fraud Can Be Steep
Scams are on the rise, but here are ways to fight back
More on Fraud
Should You Stop Using Paper Checks?
Other forms of payment may be safer as mail theft and check-washing cases surge
12 Gripping Shows and Movies About Scams to Stream Now
Stories of brazen criminals abound on Netflix, Hulu, Amazon Prime and more
What I Learned After Hackers Attacked Me and Stole $4,000
It took dozens of hours to fix the onslaught on my accounts by cyberthieves
Physical Security Keys Offer Protection from Scammers
The pros and cons of using hardware keys to secure your digital life
What to Do After You’ve Experienced a Scam
Take these steps to protect your bank accounts and personal information, and find the support you need
How Much Do You Know About P2P and Crypto Scams?
Take this quiz to see if you are savvy about tools like Zelle and Venmo, and why criminals
Glossary of Scam and Fraud Terminology
From A to Z, here’s a guide to the frequently used lingo of deception